The Importance of a Company’s Supplier Performance Risk System Score (SPRS)
Across the globe, threats continue to evolve and multiply. The cybersecurity industry is at the forefront of the movement to address those risks. The Department of Defense (DoD) has increased efforts to safeguard United States intellectual property within the Defense Industrial Base (DIB). This led to a new era of cybersecurity standards, labeled the Cybersecurity Maturity Model Certification (CMMC). A key component of DoD compliance is the Supplier Performance Risk System (SPRS) score. This self-assessment lets companies prove their cybersecurity awareness to the DoD before an in-person assessment can be conducted.
Why Organizations Need a SPRS Score
An organization’s SPRS score is necessary for three crucial reasons:
- cybersecurity risk mitigation
- competitive advantage
- resource optimization.
These aspects of operations are vital to innovation and growth, and can therefore separate an organization from its competition. Maximizing the utilization of SPRS scores can help your company prepare for the future by implementing a robust standard of policies that give prime and subcontractors an advantage when bidding on contracts involving Controlled Unclassified Information (CUI).
A favorable SPRS score indicates a hardened cybersecurity posture, therefore minimizing potential risks within the organization’s supply chain. The security and integrity of data is paramount to the DoD’s operations, and the SPRS score therefore serves as a testament to a company’s commitment to its cybersecurity. The framework required for a favorable score also provides a methodology for secure enterprise change management, ensuring continuous improvement within the organization’s environment.
Understanding the Benefit of SPRS Scores
The benefits of a strong SPRS score go beyond solidifying your organization’s cybersecurity. As the DoD seeks to further implement the CMMC architecture, organizations operating in the DIB will receive greatly increased scrutiny around their cybersecurity. It will be required for all primes and subcontractors within the DIB to provide a SPRS score if they interact with CUI or Federal Contract Information (FCI). Therefore, this requirement will propel organizations with favorable SPRS scores ahead of the competitors who neglect their cybersecurity.
Planning for the Future
By implementing the required controls, organizations will optimize auditing, create effective documentation, and reliably maintain employee awareness of cybersecurity threats. As stakeholders and partners become more aware of cybersecurity, they will place a premium on businesses who demonstrate a commitment to data protection and security. A strong SPRS score will help foster and maintain trust with partners and ensure an organization’s readiness for the future of cybersecurity.

It’s Data Privacy Week: Here’s How You can Celebrate by Protecting Your Data
Data Privacy Week is a timely annual reminder to reflect on the significance of protecting our digital footprint. The importance of safeguarding our personal information has never been more critical. This week-long initiative aims to raise awareness about privacy issues, empower individuals with knowledge, and promote responsible practices in the digital realm.
Understanding Data Privacy:
Data privacy refers to the protection of personal information therefore ensuring that individuals have control over how their data is collected, used, and shared. With the proliferation of online platforms, social media, and interconnected devices, the need to prioritize privacy has become paramount.
The Evolution of Data Privacy:
Over the years, our reliance on digital services has grown exponentially due to personal data being constantly generated and shared. Online shopping, social media interactions, online healthcare records and financial transactions, put our personal data at risk if they’re not managed appropriately. Therefore, it is imperative that the businesses we interact with every day take the proper measures to keep this data safe.
Key Themes of Data Privacy Week:
Data privacy week serves as a reminder of the need to safeguard our personal information. Therefore, it compels us to reflect on the profound impact of our digital footprint and underscores the importance of informed, proactive measures to protect our privacy. It is not merely a week on the calendar; it is a rallying call for individuals, businesses, and policymakers to prioritize and champion the fundamental right to privacy.
- Education and Awareness:
- Understand privacy rights and best practices.
- Become aware about the potential risks and consequences of data breaches.
- Cybersecurity Measures:
- Highlight the importance of strong passwords and multi-factor authentication.
- Encourage individuals among organizations to stay vigilant against cyber threats.
- Legislation and Regulation:
- Raise awareness of current privacy laws and regulations.
- Digital Hygiene:
- Emphasize the importance of regularly updating software and being cautious about sharing sensitive information.
- Corporate Responsibility:
- Recognizing the role of businesses in protecting customer data.
- Encouraging transparent data practices and responsible data handling.
What We Can Do As Individuals
Data Privacy Week encourages us to take an active role in protecting our own data. This includes being mindful of the information shared online therefore understanding privacy settings on various platforms, and staying informed about potential risks.
A Call to Protect Our Digital World
As we observe Data Privacy Week, we can all collectively commit to a culture of responsible data usage. Therefore, by embracing awareness, education, and proactive measures, we can create a digital environment where privacy is upheld as a fundamental right. Learn how USX Cyber utilizes the XDR platform, GUARDIENT™™ to detect threats before they ever reach your personal data.

Don’t get Hooked: The Dangers of Phishing
One prevalent threat that internet users face is phishing—a malicious attempt to trick individuals into divulging sensitive information. Technology connects us all, however, the darker side of the digital realm has become increasingly sophisticated. As we immerse ourselves in the vast sea of cyberspace, it is crucial to be aware of the dangers lurking beneath the surface and equip ourselves with the knowledge to avoid falling victim to phishing attacks.
What is Phishing?
Phishing is a cybercrime technique where attackers masquerade as trustworthy entities, hoping to capture sensitive information such as usernames, passwords, and financial details. This deceptive practice is often carried out through seemingly legitimate emails, messages, or websites that prompt users to click on malicious links or provide confidential information.
The Dangers:
As technology advances, so do the tactics employed by cybercriminals to exploit unsuspecting individuals. From identity theft to financial loss, phishing is a digital predator that preys on trust and exploits the human element of online interaction. Understanding the dangers of phishing is paramount in fortifying our defenses against these deceptive schemes and safeguarding the digital landscapes we navigate daily.
Identity Theft: Phishing attacks can lead to identity theft, as cybercriminals use stolen information to impersonate individuals, gaining unauthorized access to their accounts and personal data.
Financial Loss: Phishing attacks frequently target financial information. Falling for these scams may result in unauthorized transactions, drained bank accounts, and credit card fraud.
Ransomware Attacks: Some phishing attempts aim to infect devices with ransomware, locking users out of their systems until a ransom is paid.
Compromised Credentials: Phishing often involves tricking users into revealing login credentials. Once obtained, these credentials can be used to compromise other accounts that share the same or similar login information.
How to Avoid Falling for Phishing Attacks:
As we navigate through the digital age, fortifying ourselves against the artifice of cybercriminals becomes a paramount endeavor. By staying informed and adopting vigilant practices, we can collectively strengthen our defenses and safeguard against the ever-present risks lurking in the virtual domain.
- Be Skeptical of Emails and Messages:
- Verify the sender’s email address.
- Be cautious of unexpected emails or messages, especially those urging immediate action.
- Check Website Authenticity:
- Before entering sensitive information, ensure the website’s URL is legitimate.
- Look for secure connections (https://) and padlock symbols in the address bar.
- Use Two-Factor Authentication (2FA):
- Enable 2FA whenever possible to add an extra layer of security to your accounts.
- Educate Yourself and Others:
- Stay informed about the latest phishing techniques.
- Educate friends, family, and colleagues about the dangers of phishing.
- Install Reliable Security Software:
- Use reputable antivirus and anti-malware software to detect and block phishing attempts.
- Regularly Update Software:
- Keep your operating system, browsers, and security software up-to-date to patch vulnerabilities.
- Verify Requests for Sensitive Information:
- Contact the supposed sender through a known, reliable channel to verify the legitimacy of requests for sensitive information.
Phishing is a persistent threat that targets individuals across the digital landscape. However, by staying vigilant, educating ourselves and others, and implementing security best practices, we can navigate the online world with greater confidence and reduce the risk of falling victim. Remember, a well-informed and cautious approach is the best defense against the treacherous currents of cybercrime. Reach out to one of our USX Cyber experts to learn how you can implement changes to protect your organization.

Safeguarding the Digital Perimeter: A Deep Dive into Network Intrusion Detection Systems
Network Intrusion Detection Systems (NIDS) are a critical component in the cybersecurity arsenal. In this blog, we unravel the intricacies of NIDS, exploring its significance, functionalities, and the pivotal role it plays in fortifying digital landscapes.
Understanding the Network Intrusion Detection System
NIDS is a vigilant guardian, tirelessly monitoring network traffic for suspicious activities or potential security threats therefore, unlike traditional firewalls that focus on traffic filtering, NIDS delves deeper, analyzing packet-level data, which are fragments of data that are broken down when transferred. This is done to identify patterns indicative of malicious behavior.
Key Functionalities of Network Intrusion Detection Systems
1. Signature-Based Detection: Utilizing a database of predefined attack signatures, NIDS compares incoming traffic against these patterns. If a match is found, an alert is triggered, signaling a potential intrusion.
2. Behavioral Analysis: NIDS goes beyond signatures thereby employing behavioral analysis to identify deviations from normal network behavior. This dynamic approach is crucial for detecting novel threats not covered by signature-based methods.
3. Real-time Monitoring: NIDS operates in real-time thus providing instantaneous alerts upon detecting suspicious activities. This rapid response capability is instrumental in mitigating the impact of cyber threats.
Deployment Strategies
NIDS play an important role in safeguarding digital environments from malicious activities. Various deployment strategies exist to effectively integrate NIDS into a network infrastructure. The choice of deployment strategy depends on the specific security requirements such as network architecture, and performance considerations of the organization implementing the NIDS.
1. Inline vs. Passive Deployment: NIDS can be deployed either inline or passively. In inline deployment, the system actively blocks malicious traffic, while passive deployment focuses on monitoring without direct intervention. The choice depends on the organization’s security requirements and risk tolerance.
2. Placement within the Network: Strategic placement of NIDS sensors is vital because they can be positioned at critical junctures within the network architecture, such as at the perimeter, in data centers, or between network segments, to ensure comprehensive coverage.
Challenges and Considerations
Implementing and maintaining an effective NIDS comes with its own set of challenges and considerations. From the ever-growing sophistication of cyber threats to the need for seamless integration into complex network architectures, organizations must navigate a myriad of factors to ensure the efficacy of their intrusion detection systems.
1. False Positives: NIDS may trigger alerts for benign activities which therefore leads to false positives. Fine-tuning and regular updates to the signature database help minimize this challenge.
2. Encryption: The rise of encrypted traffic poses a challenge for NIDS, as it limits the system’s ability to inspect payload contents. Implementing SSL/TLS decryption mechanisms can help address this issue.
The Future of Network Intrusion Detection Systems
As cyber threats evolve, so must our defense mechanisms. The future of NIDS lies in machine learning and artificial intelligence, empowering systems to adapt and learn from emerging threats autonomously. In the ever-expanding digital realm, a robust Network Intrusion Detection System stands as a stalwart guardian, protecting against the relentless tide of cyber threats. Make sure to reach out to one of our USX Cyber experts to discuss how you can implement NIDS within your organization.

Shielding the Fortress, Small Business Cybersecurity
Small businesses are increasingly becoming targets for cyber threats, and not just in the U.S. Australia has recently committed $18.2 million to perform small business cybersecurity health checks. In Australia alone, cyber attacks against small businesses cost the economy an estimated $2 billion per year.
Regardless of size, small companies still handle sensitive customer data, financial transactions, and proprietary information that make them attractive to cybercriminals. As a result, it’s imperative for small businesses to prioritize cybersecurity measures to protect their operations, reputation, and customer trust. At USX Cyber, we understand that tackling the operational matter of cybersecurity can feel overwhelming, so therefore we’ve put together a few key components specifically for small businesses that will help in fortifying your digital defenses.
Understanding the Threat Landscape
Small businesses may be under the misconception that they are too insignificant to attract cybercriminals. However, statistics show that they are often the preferred targets due to their typically weaker security measures. The common cyber threats faced by small businesses include phishing attacks, ransomware, and data breaches.
Conduct a Risk Assessment
Begin by conducting a thorough risk assessment to identify potential vulnerabilities and threats specific to your business. Evaluate the types of data you handle and thereby assess potential entry points for cybercriminals, and analyze the impact of a security breach on your operations.
Implement Robust Password Policies
Weak passwords are a common entry point for cyberattacks. Encourage the use of strong, unique passwords and implement multi-factor authentication (MFA) wherever possible. Regularly update passwords and educate employees about the importance of password hygiene.
Enforce Employee Training and Awareness
Your employees are the first line of defense against cyber threats. Provide comprehensive cybersecurity training to educate them about the latest threats, safe online practices, and how to recognize phishing attempts. Foster a culture of security awareness to instill a sense of responsibility among your team.
Secure Networks and Devices
Ensure that your network is secured with a robust firewall, and encrypt sensitive data during transmission. Keep all software, including antivirus programs, up to date. Regularly patch and update operating systems and applications to address vulnerabilities.
Implement Data Backup and Recovery
Implement a regular data backup strategy to prevent data loss in the event of a cyberattack. Store backups in a secure, offsite location, and regularly test the restoration process to ensure it functions effectively.
Secure Customer Transactions
If your small business handles financial transactions, prioritize the security of customer payment information. Use secure payment gateways, encrypt transaction data, and thereby comply with relevant industry regulations such as PCI DSS (Payment Card Industry Data Security Standard).
Collaborate with Cybersecurity Professionals
Consider enlisting the services of cybersecurity experts or outsourcing your cybersecurity needs in order to gain a reputable provider. Professionals can conduct regular assessments, implement advanced security measures, and keep your business abreast of the latest threats and best practices.
Develop an Incident Response Plan
Develop a comprehensive incident response plan outlining the steps to be taken in the event of a security breach. Assign roles and responsibilities, establish communication protocols, and conduct regular drills to ensure your team is well-prepared to handle a cyber crisis.
An Investment in Cybersecurity is an Investment in Your Business’ Operational Health
Investing in small business cybersecurity is not just a precautionary measure; it’s a fundamental aspect of safeguarding your business in the digital age. By prioritizing cyber health, you not only protect your data and assets, but also demonstrate to your customers that their trust and privacy are paramount. Stay vigilant, stay informed, and fortify your digital fortress to ensure the long-term success and resilience of your company in an ever-evolving online landscape.

Navigating the Digital Terrain
In an interconnected world, the supply chain is the backbone of technological ecosystems. With this interconnectedness comes a growing number of vulnerabilities, making robust cybersecurity supply chain risk management imperative.
Understanding the Threat Landscape in Cybersecurity Supply Chain
The supply chain is a complex web, encompassing hardware, software, and services. Threat actors hunt for and exploit vulnerabilities at various points, posing risks that can result in data breaches, system compromises, and even economic espionage. To effectively manage these risks, organizations must adopt a proactive stance. Here are a few ways to help your company avoid falling victim.
Identifying Key Risk Factors in Cybersecurity Supply Chain Risk Management
1. Assess and Monitor Third-Party Vendors: A compromise in any link of the supply chain can have a domino effect, affecting the entire ecosystem.
2. Verify Software Integrity: This practice is essential to prevent the introduction of malicious code. Regular audits and code reviews contribute to maintaining a secure software supply chain.
3. Physical Security: Protecting the physical components of the supply chain, from manufacturing to delivery, is often overlooked. Unauthorized access during any phase can compromise the integrity of the entire process.
Implementing Risk Mitigation Strategies
1. Supply Chain Mapping: Develop a comprehensive map of your supply chain to identify critical components and potential points of vulnerability. This visibility enhances the ability to respond promptly to any security incidents.
2. Threat Intelligence Integration: Proactively address emerging risks before they manifest in the supply chain.
Cybersecurity supply chain risk management is not merely a necessity but a strategic imperative. By understanding, assessing, and proactively mitigating risks, organizations can fortify their digital supply chains, safeguard sensitive data, and contribute to a more secure digital ecosystem.

High Cost of Data Breach
vs. Investment In Preventative Cybersecurity Measures
Data is one of the most valuable assets for small and medium sized companies, which is why taking the proper steps to protect it is so critical. And as our reliance on technology increases, the risk of cyber attacks equally grows. Breaches from cyberattacks can be catastrophic, especially for small and medium sized businesses without the resources to shoulder the financial consequences. In this post, our industry experts share a window into the staggering costs associated with a data breach and contrast that with the relatively low expense of an affordable, flexible preventative cybersecurity measures.
The Soaring Cost of Data Breaches
Direct Financial Impact
The substantial financial impact of data breaches hits a company both directly and indirectly. These costs can be categorized into several areas:
1. Direct Financial Losses: The expenses related to investigating and containing a breach, recovering lost data, and compensating affected individuals for their losses are daunting. On average, a small or mid-sized company can expect to spend $38,000 to recover from a single security breach.
2. Legal and Regulatory Costs: Companies may face hefty fines and legal fees for failing to comply with data protection regulations, such as GDPR or HIPAA, and for failure to disclose a breach.
3. Reputation Damage: The negative perceptions from a data breach can be long-lasting. Customers often lose trust, leading to reduced sales, customer churn, and damage to a company’s brand reputation.
4. Operational Disruption: Data breaches can disrupt business operations, leading to downtime, productivity losses, and increased recovery costs.
Hidden Costs
In addition to the immediate financial impact, there are often less obvious but equally impactful costs of data breaches including:
1. Forensic Investigations: Companies may need to hire cybersecurity experts to determine the scope and cause of the breach.
2. Customer Outreach and Support: Informing affected customers can be costly, both in terms of communication expenses and potential credit monitoring services.
3. Crisis Management: Properly handling the effects of a breach and rebuilding trust with stakeholders requires considerable resources.
The Low Cost of Preventative Cybersecurity Measures
While data breaches can be financially devastating, the good news is that most breaches are preventable through proactive and relatively low-cost cybersecurity measures. Basic preventative measures include:
1. Regular Updates and Patching: It’s important to keep software and systems up-to-date to protect known vulnerabilities that hackers often exploit.
2. Firewalls and Intrusion Detection Systems (IDS): These tools help continuously monitor network traffic and block suspicious activity.
3. Encryption: Encrypting sensitive data both at rest and in transit can make it extremely difficult for unauthorized users to access valuable information.
4. Incident Response Plan: It’s essential to develop a clear and efficient plan in the case of an attack that can effectively minimize the impact of a breach if one does occur.
5. Security Audits: Regular security audits and vulnerability assessments will identify weaknesses before they are exploited.
The team at USX Cyber offers solutions that employ these safeguards and many others, in order to provide essential and accessible security for small and medium sized businesses. We welcome you to contact us for more information, to set up a free assessment or to discuss your company’s cybersecurity and compliance needs.

Cybersecurity Awareness Month: Protecting Your Digital World
October is synonymous with the beginning of Fall, but it’s not just about Halloween and changing colors. October is also Cybersecurity Awareness Month and an important time to remember that hackers and cyber attacks targeting businesses across the U.S. are more than just scary stories. Cybersecurity Awareness Month is an opportunity for companies to take another look at how they are securing their businesses from the many evolving risks threatening their operations. By actively participating in this initiative, businesses can better protect their assets, ensure they meet the latest regulatory requirements, and maintain the hard-earned trust of their customers.
Ways To Participate
Here are a few ways you can take advantage of this helpful reminder to reinforce your defenses and help spread the word:
1. Protect Assets
A company’s data, intellectual property, and customer information are invaluable assets. Participating in Cybersecurity Awareness Month helps you establish robust defenses to safeguard these critical resources. Specifically, you can conduct cybersecurity assessments to identify vulnerabilities in your systems and network. In addition, you can restrict access to critical systems and data on a need-to-know basis.
2. Stay Current on Compliance Requirements
Various industries have stringent regulations regarding data security. Falling short of compliance can lead to hefty fines and legal troubles. This Awareness Month, businesses can demonstrate their commitment to meeting these requirements. One way to show that commitment is to employ or designate a dedicated cybersecurity team responsible for implementing compliance measures.
3. Enhance Brand Trust
Customers and clients trust businesses that prioritize their data security. Engaging in cybersecurity awareness initiatives not only sends a signal to your clients that you take their privacy seriously, but also enhances their trust in your brand.
4. Educate Your Workforce
Use some time this month to organize training sessions to raise cybersecurity awareness among employees. Teach them about the importance of strong passwords, recognizing phishing attempts, and safe online practices.
5. Update Your Incident Response Plan
When’s the last time you looked at your plan in case of a cyber attack? Make sure that you have an up-to-date and comprehensive incident response plan that meets current threats and will be sure to minimize damage in case of a cyberattack.
Cybersecurity Awareness Month is a catalyst for companies to reevaluate their digital defenses and take proactive steps to protect their sensitive data, operations, and reputation. In a world where cyber threats are constantly evolving, being vigilant is essential for businesses of all sizes. Your company’s security and reputation are worth the investment. By setting up the latest cybersecurity tools and technologies, including firewall systems, intrusion detection, antivirus software, encryption, and real-time monitoring, you can protect your digital assets. If you need a partner to help, USX Cyber is here to be an extension of your team.
Top 10 Questions We’re Asked Most About CMMC
Updated September 6, 2023
With the recent news from the DoD surrounding CMMC codification, many businesses are revisiting what compliance may look like in the upcoming months. Without final rules being shared up to this point, there’s still a lot of unknowns that are paralyzing business leaders from taking action.
We asked our team of experts what questions they’re seeing come up most often and the advice they give to our customers at USX Cyber.

1. What is CMMC, and why is it important for government contractors?
CMMC, or the Cybersecurity Maturity Model Certification, is a framework introduced by the DoD to enhance cybersecurity practices in the defense supply chain. It’s essential because it ensures that organizations handling Controlled Unclassified Information (CUI) maintain a strong cybersecurity posture, protecting sensitive data and national security.
2. When will CMMC become a requirement for defense contracts?
The timeline has varied over the past few years but with the DoD’s recent update and its submission to the Office of Management and Budget for review, we can expect to see this appear in the next year or so. While there’s still time to get compliant, it’s best not to wait much longer. Getting compliant ahead of time ensures that you won’t fall behind on new contracts and can make your business a more competitive option for current bids knowing that compliance is already taken care of.
3. How does CMMC differ from NIST SP 800-171?
CMMC builds upon NIST SP 800-171 by adding more depth and specificity to cybersecurity requirements. It introduces three levels of maturity, indicating a progression in security practices, and focuses on safeguarding Controlled Unclassified Information (CUI). At this time, CMMC is applicable only to contractors currently working or planning to work with the DoD, while NIST 800-171 covers businesses that may not be working with the DoD but still deal with CUI.
4. What level of CMMC certification do I need?
The specific CMMC level required depends on the type of contracts you have or plan to pursue. The DoD will specify the required level in the Request for Proposal (RFP) or contract. It’s important to align your cybersecurity efforts with these requirements. You should also note that the level of compliance in the contract may not apply to all of the subcontractors producing work under that RFP. Each contractor will only need the level of compliance aligned with the data that they specifically work with, not what’s defined in the contract as a whole. For example, if a prime contractor requires compliance at Level 3, but they’re only passing Federal Contract Information to their subcontractors to complete a certain aspect of the contract, that subcontractor only needs to be certified at a Level 1.
5. How do I prepare for a CMMC assessment?
Subcontractors should really start by understanding the most up-to-date CMMC requirements and aligning their cybersecurity practices from there. Reviewing resources such as USX Cyber’s CMMC Webinar from earlier this year can help build and renew that necessary context. Once a business better understands this new rulemaking, it’s a good idea to conduct a self-assessment to identify gaps and areas needing improvement. USX Cyber also provides a free consult to review your current cybersecurity practices and the CMMC gaps you may need to address.
6. What’s the role of a Certified Third-Party Assessor Organization?
C3PAOs conduct official assessments to determine an organization’s level of CMMC compliance. They evaluate your cybersecurity practices, policies, and controls to ensure they align with the requirements of the chosen CMMC level. A third-party assessor will be required for Level 3 compliance needs. Partnering with USX Cyber also provides access to our recommended assessors who will assist with compliance roadmapping alongside our team of experts.
7. How can my organization demonstrate CMMC compliance?
In order to demonstrate compliance, you’ll need to have full understanding and documentation of how your business satisfies the requirements for CMMC. This documentation and necessary expert support should come standard with any cybersecurity provider you’re working with. At USX Cyber, you gain direct access to our team of experts to provide the necessary documentation and controls when it’s necessary to demonstrate your compliance.
8. Can subcontractors be held liable for non-compliance?
Yes, subcontractors will be held liable for non-compliance with CMMC requirements. Prime contractors and the DoD prioritize secure supply chains, which means compliance expectations extend to all tiers of the supply chain, including subcontractors. In fact, it’s common for many prime contractors to request or prefer subcontractors that are already compliant even though the rule making hasn’t been formally codified at this time.
9. What if we’re not ready for CMMC by the time contracts require it?
Non-compliance could lead to missing out on valuable contract opportunities which is why it’s important for businesses to consider and prepare for compliance now. Simply put, your business isn’t eligible to bid on contracts that require CMMC until you’re compliant and this includes acting as subcontractors for primes that are bidding on relevant RFPs.
10. How can I ensure continuous compliance as regulations evolve?
It’s always a good idea to stay up-to-date with industry news and changes. However, it can be a lot to stay on top of a business as well as regulations and their complexities. Finding a cybersecurity partner who keeps status for you ensures you can focus on what really matters for your business. The team at USX Cyber not only stays up to date with compliance changes and needs, our own platform adapts and improves when there are changes. Making sure we not only know what’s coming up but also our customers are protected without even having to think about it.
What can I do now?
As details become formalized and updates are released, our team of compliance specialists will be sharing them regularly. Be sure to get in touch with a USX Cyber team member to talk more about how you can proactively prepare, learn what CMMC may mean for your business, and receive updates on this and other important cybersecurity topics.
Don’t let the unknown stall out the growth and operations of your business. By developing a deeper understanding of CMMC, you can ensure you’re ready for the change in upcoming contracts and bids.
What Subcontractors Need to Understand About the Three Levels of CMMC 2.0
The Cybersecurity Maturity Model Certification (CMMC) program continues to evolve, bringing significant changes and implications for businesses operating within the Defense Industrial Base (DIB). As the rulemaking process progresses and updates are introduced, it becomes crucial for subcontractors in the DIB to stay informed about these changes and understand the key points that can impact their operations. Let’s walk through the essentials of CMMC to better understand its evolution and the key aspects subcontractors in the DIB should be aware of.
CMMC 2.0 Explained
CMMC is a framework established by the U.S. Department of Defense (DoD) to assess and enhance the cybersecurity posture of organizations within the DIB. It aims to protect sensitive information and ensure that adequate cybersecurity practices are in place throughout the contractor supply chain.
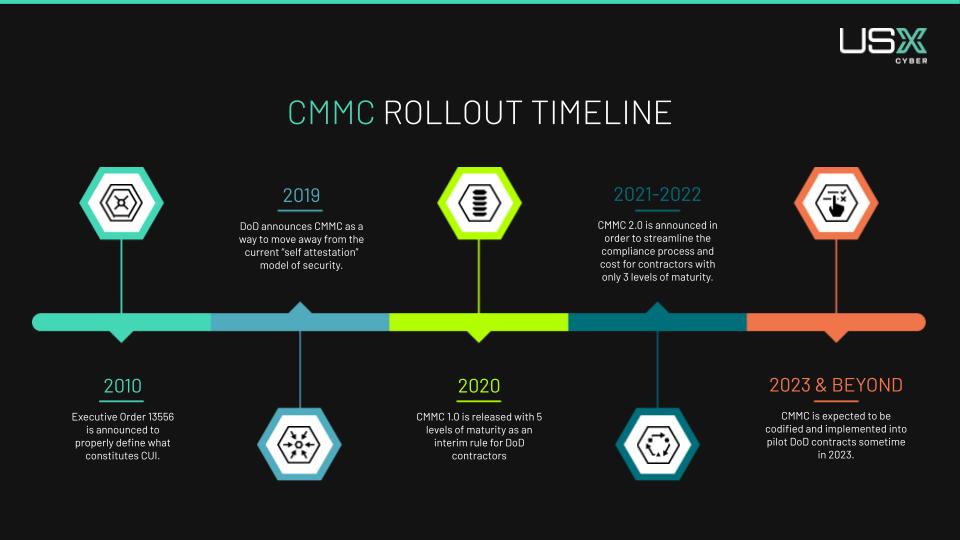
As the CMMC program evolves, it is essential to stay up-to-date. Currently, we’re still waiting for the rulemaking process to complete as the requirements and implementation guidelines for CMMC are finalized. The DoD releases updates and news as they have new developments, but it has proven to be a challenge for businesses to navigate, especially when it comes to which requirements they need to meet. Here is what we know so far about this process.
The CMMC framework originally consisted of five levels, each representing an increasing level of cybersecurity maturity. This has since been reduced to 3, with Level 3 controls yet to be finalized. Contractors will be required to meet specific requirements outlined in one of these levels based on their involvement in handling sensitive DoD information.
To oversee the certification process, training, and assessment of contractors, the CMMC Accreditation Body (CMMC-AB) was established. They work with Certified Third-Party Assessment Organizations (C3PAOs). C3PAOs play a crucial role in assessing and certifying organizations’ compliance with CMMC.
That being said, we still don’t have a concrete date for when this framework will be codified and start appearing in new DoD contracts. In the meantime, we are seeing prime contractors starting to proactively enforce compliance among their subcontractors. This is to ensure a seamless transition once CMMC is released, and that all partners are doing their due diligence when it comes to protecting our most important information.
CMMC Levels and Subcontractors
It may feel daunting to subcontractors understanding each level of CMMC and the required controls, on top of assessment and ongoing support. While the framework is still waiting to be codified, we do know that each contractor will only need the level of compliance aligned with the data that they specifically work with, not what’s defined in the contract as a whole. For example, if a prime contractor is compliant at Level 3, but they only pass FCI data to their subcontractors, that subcontractor only needs to be certified at a Level 1.
So, what do all the levels entail? And which one is right for your business? We’ve outlined them below to help you get started.
Level 1
At Level 1 certification within the CMMC framework, organizations in the defense industrial base are expected to have basic cybersecurity practices in place. It consists roughly of 17 controls and is for organizations that only process federal contract information. This is intended for contractors only working with Federal Contract Information (FCI). At this level, you can self-assess.
Level 2
Level 2 certification is meant for organizations processing controlled unclassified information (CUI) data. At this level, organizations will be expected to meet at least 110 controls derived from NIST SP 800-171. Organizations at this level will also require an assessment from an approved and authorized third-party provider.
Level 3
While Level 3 controls have yet to be finalized, the government is actively working to define these at the time of publishing this article. This level is intended for organizations who process CUI data but at a higher, more sensitive nature. As of now, we know that at a minimum Level 3 contractors will need to follow 110+ security practices based on NIST SP 800-171 and -172. Assessments at this level will also go through a government-led assessment, rather than a self-assessment or working with a third-party.
What’s Next for CMMC?
As the CMMC program continues to evolve, businesses within the DIB must stay well-informed about the framework and its evolving updates. By staying engaged and keeping track of the direction of this framework, subcontractors can signal trust to their clients and partners, continually enhance their cybersecurity posture, and ensure compliance readiness.
Our best advice is to stay proactive. If you are overwhelmed or unsure of how this process may affect your business, you can engage with a trusted cybersecurity partner like USX Cyber, and leverage our expertise to support your CMMC journey. To start, check out our webinar on CMMC for more information or reach out to our experts directly so we can help protect sensitive information, strengthen the defense supply chain, and contribute to a more secure future.
Remember, CMMC compliance is not a one-time task but an ongoing commitment to maintaining robust cybersecurity practices within the Defense Industrial Base.













