7 Ways to Mitigate Your Business’ Cyber Risk
As a small business owner, you are keenly aware of the many risks your company faces. However, one of the most often overlooked of these risks is cyber security. Despite being one of the most common threats, businesses often do not take the necessary precautions to protect themselves from a cyber attack.
Hackers are always coming up with new ways to exploit vulnerabilities, so it’s important to take steps to protect your business. Here are 7 ways to mitigate your cyber risk:
- Perform a cybersecurity risk assessment
- Install a firewall and keep it up-to-date
- Use strong passwords and change them regularly
- Educate your employees about cyber security best practices
- Consistently update and upgrade your software and systems
- Reduce your attack surface
- Monitor your network for suspicious activity
While there are many cybersecurity measures you can take, implementing even a few of these tips can drastically help reduce your chances of becoming the next victim of a cyberattack.
1. Perform a cybersecurity risk assessment.
A cybersecurity risk assessment is an important tool for businesses to identify areas of vulnerability in their systems and networks. By conducting a robust risk assessment, businesses can identify potential threats and vulnerabilities, and develop plans to mitigate or reduce those risks. Risk assessments can help businesses to better understand their cybersecurity posture and make informed decisions about how to protect their data and systems.
When conducting a risk assessment, businesses should consider the potential impact of a breach, the likelihood of a breach occurring, and the costs associated with recovering from a breach. Risk assessments can be conducted internally or externally, and should be tailored to the specific needs of the business.
2. Install a firewall and keep it up-to-date
A firewall is a critical component of any organization’s cyber security strategy. It helps to protect your network from external threats and can be configured to allow or deny access to specific services and applications. However, your firewall must be kept up to date with the latest security patches and updates to be most effective.
Just as importantly, organizations should also consider implementing a next-generation firewall (NGFW) which offers advanced features such as application control and intrusion prevention. NGFWs can provide a higher level of protection against sophisticated cyber attacks.
3. Use strong passwords and change them regularly
Another way to mitigate the risk of infiltration into your business is to use complex passwords. By using a password that is difficult to guess, you make it more difficult for hackers to gain access to your system.
You can also deploy multi-factor authentication strategies. This means that in addition to a passwordyou will also need another form of identification, such as a fingerprint or an iris scan, to gain access to your system.
A strong policy is just as important as strong passwords.Your policy should discourage password sharing among employees. Not doing so creates a security risk by allowingmultiple people to know the password to a given account. It also makes it difficult to keep track of who is using which password. Finally, if an employee leaves the company, any passwords they know should be changed to prevent them from accessing company information.
4. Educate your employees about cyber security best practices
The best way to mitigate your business’ cybersecurity risk is to train employees regularly on how to identify and avoid cybersecurity threats. By doing so, you can ensure that your employees are aware of the latest threats and know how to protect your business’ data.
Phishing emails are a common risk to your employees and the importance of identifying phishing attempts cannot be understated because of the damage it can cause to your business. Phishing is a type of online fraud that occurs when an attacker tries to trick a victim into providing personal information or financial data. This information can then be used to commit identity theft or other crimes.
Unfortunately, phishing attacks are becoming more sophisticated and harder to spot, so it’s important that your employees know how to identify them. Providing proper training to ensures your employees don’t leave the door open to hackers..
5. Consistently update and upgrade your software and systems
One of the most important things you can do to protect your business from cybercriminals is to apply software updates as soon as they are available. Cybercriminals are constantly looking for ways to exploit vulnerabilities in software, and if you don’t have the latest security updates installed, you could be at risk. That’s why it’s important to check for updates regularly and install them immediately..
To help with this effort, most service and software providers release patches on a regular schedule. Cybercriminals are aware of this and often target organizations that have not implemented an effective patch management schedule. By being aware of when their service or software providers typically release patches, organizations can create an effective patch management schedule and help protect themselves from attacks.
6. Reduce your attack surface
The term “attack surface” refers to the areas of vulnerabilities or entry points that cybercriminals can use to access sensitive information and data. The larger the attack surface, the greater the risk of a successful attack. To reduce the attack surface, organizations need to identify and eliminate as many potential entry points as possible. This can be accomplished through a variety of security measures, including firewalls, intrusion detection/prevention systems, and access control lists. Attack surface reduction is a critical element of any effective security strategy.
An organization’s attack surface can be divided into three categories:
- External attack surface: This includes anything that is publicly accessible, such as websites, email servers, and DNS servers.
- Internal attack surface: This includes anything that is accessible from within the organization’s network, such as file servers, databases, and application servers.
- Endpoint attack surface: This includes anything that is connected to the organization’s network, such as laptops, smartphones, and printers.
The goal of attack surface reduction is to minimize the exposure of all three categories listed above. By doing so, organizations can significantly reduce their risk of a successful cyberattack.
7. Monitor your network for suspicious activity
Being proactive is one of the most effective strategies for mitigating cybersecurity risk. By taking proactive steps to secure your systems and data, you can significantly reduce the likelihood of a successful attack. Implementing strong security controls, such as multi-factor authentication and data encryption, can make it much more difficult for attackers to gain access to your systems and data.
At USX Cyber, we provide advanced cybersecurity, before you need it.. We are able to do that because our GuardientTM platform leverages the most-advanced cybersecurity technologies under the watchful eyes of our US-based analysts. This means your business will be the “first to act” vs. the “last to know” when it comes to cybersecurity threats.
Protect Your Business Today
While following these tips can’t guarantee that your business will be impervious to a cyberattack, they will help you mitigate the risk and make it less likely that your company will be compromised. However, if you’re like many small businesses, you might lack the time, resources or staffing to put these tips into practice. We can help. Contact USX Cyber today and find out how easy it is to get powerful, 24/7 protection that is scaled to fit your business.
How to Securely Manage a Remote Workforce
It wasn’t too long ago that having a remote workforce was the exception. Now, that exception is fast becoming the rule. In fact, the U.S. Census Bureau noted that the number of people primarily working remotely from home has nearly tripled since 2019.
Unfortunately, hackers have taken notice of this growing trend. As more and more companies of all sizes have opened their environments to accommodate remote workers, they’ve often unintentionally opened the door to huge cybersecurity risks.
However, by following our remote work from home security tips you can help ensure your business is set up for success no matter what the future of work looks like.
Top 10 Cybersecurity Tips for Remote Employers
Few, if any, companies were ready for this massive shift to remote work, leaving many IT departments having to play a high stakes game of catch-up. And despite taking proper precautions, shoring up cyber defenses, and following best practices — the overarching truth remains — your people are your greatest cyber risk. Whether that’s through clicking a malicious link from a hacker, or simply not adhering to company security policies, every action by your employees is amplified in this new world of remote work.
But if you follow these 10 actionable cybersecurity tips from our expert USX Cyber analysts, you can help your company and the employees you manage stay protected.
- Work computers are for work only
- Enable user authentication
- Use a VPN
- Have strong password rules
- Keep personal devices off the company network
- Use centralized storage
- Safeguard videoconferences
- Stay on top of software updates
- Follow email best practices
- Establish a cybersecurity plan
1. Work computers are for work only
When remote workers bring a company device home, there may be the temptation to allow other household members (or kids!) to use a laptop, cellphone or other hardware for personal purposes. However, for fairly obvious reasons, this can spell disaster by exposing your network to threats and even unauthorized use of confidential or sensitive files. Yet, this is a fairly easy solution. By making sure your company policy addresses third-party use of company assets, you can avoid this issue.
2. Enable user authentication
Multifactor authentication is a critical tool in defending your network from major security risks. Ideally, remote employees should be required to verify their identity before accessing company data or network resources.
3. Use a VPN
Relying on the security of an individual employee’s network is a dicey proposition at best. VPNs allow secure remote access to company resources, provide encrypted connections and allow access control for your network. They are not a perfect solution. But when combined with these other remote work from home security tips, it can provide a strong layer of protection.
4. Have strong password rules
It’s 2022, and unbelievably “123456” is still the most commonly found password on the dark web, due to data breaches. There are a few simple guidelines you can have your employees follow to strengthen their passwords. This includes using random words and letters, mixing upper and lower case characters, and avoiding passwords that contain dates of birth or nicknames. But an even better plan is to invest in a password manager to keep track of all your employees’ passwords and have them safely stored in an encrypted digital vault.
5. Keep personal devices off the company network
It might not seem like a big risk to allow remote workers to use their personal devices to access your network. But even with antivirus software, password protection, and VPNs — allowing employees to use their own devices on your network is a major oversight. Many of these devices can have outdated software, no password protection or viruses of their own. The best policy here is to require your remote workforce to only use company-issued devices to conduct work-related tasks.
6. Use centralized storage
More and more companies have migrated their files and resources to the cloud, and for good reason. Centralized storage solutions protect files and data via an attached firewall. But when remote employees store files locally, on their devices, data can be lost if that device is compromised or destroyed. Having centralized storage is important, but educating your employees on how to use it is just as crucial.
7. Safeguard videoconferences
Kindly put, meetings can be an acquired taste. And while the new work from home reality has dictated we meet with each other via video conferencing software, it doesn’t come without cybersecurity risks. Since the start of the remote work shift, hackers have been infiltrating video conferences to monitor and gather sensitive company information. On top of that, these “Zoom Bombing” attacks can prove to be quite upsetting to your employees. This means that you need to set up private meetings that are password protected and control guest access through a virtual waiting room.
8. Stay on top of software updates.
You might be picking up on a theme — the simplest security measures are often the most important. Updating software and devices is a huge factor in ensuring your work from home security plan is successful. While most software today will automatically check for security updates and apply them, you still may need to have access to your employee’s remote devices to complete the update fully.
9. Follow email best practices
91% of all cyber attacks start with a phishing email. And while using your company’s inbox against you is one of the most tried and true tactics in a hacker’s toolbox, there are steps you can take to shore up your security. That starts with having robust antivirus software monitoring this attack vector. However, the most important thing you can do when managing your remote workforce is to educate your employees about the dangers and how to spot potential email threats. The old adage holds true, only open email attachments that you are expecting, no matter who sent them.
10. Establish a cybersecurity plan
The number one tip we at USX Cyber give to a potential client is always the same — educate your entire organization on cybersecurity. That starts with having solidified policies, plans, and procedures in place. We’ve seen it time and again be the action that separates successful companies from vulnerable companies. However, it’s critical to ensure these cybersecurity policies are easily understood by every employee. So when you’re building your plan, make sure you frame it with language that is clear and applicable to your remote employee’s workday.
Protect Your Business Today
At USX Cyber, we’ve built our GuardientTM cybersecurity platform to provide small businesses with powerful protection in this new remote working reality. Simply put, the days of treating cybersecurity as optional are over. And just like the internet and email are essential to running a business, the same now goes for having cybersecurity.
With GuardientTM you can have access to the same level of protection the big corporations are using to protect their businesses from remote working risks. But our scalable, flexible, and extensible services make sure you get state-of-the-art cybersecurity that fits both your budget and protection needs.
Talk with a USX Cyber analyst today and let’s navigate this new world together.
What You Don’t Know Will Hurt You: Understanding Real-Time Cyber Telemetry
Data is the very lifeblood of businesses big or small — from the financial data that helps steer organizational decisions to the customer data you are charged with safekeeping. But data is also your best defense against cyber attackers. That is if you know how to harness it correctly.
Real-time cyber telemetry is how USX Cyber puts your data to work and helps you stay protected in today’s environment of rapidly evolving cyber threats. Simply put, real-time cyber telemetry is the collection of data across multiple points such as endpoints (individual computing device), a network, email server, and the cloud to actively aid in the detection and hunting of cyber threats.
This is the foundation for our leading-edge Guardient Extended Detection and Response (XDR) cybersecurity platform. By gathering comprehensive security data from your organization as a whole, we are able to get a much more complete picture of your network than a traditional Endpoint Detection and Response (EDR) model could ever provide (more on that in a second). Guardient also brings together industry-leading tools and Analysts to provide instant, actionable insights to help defend your business against hackers and other threats.
Let’s take a deeper look at why XDR and telemetry provide unmatched protection.
More Data is Needed
Traditional cybersecurity products have generally fallen under the umbrella of the EDR model. In this defense posture, an agent is installed locally on a system, and alerts are captured only for the endpoint that is being monitored. This is known as a Host Intrusion Detection System (HIDS) and it is a very common practice in the cybersecurity industry. And there’s nothing theoretically wrong with this methodology. HIDS has the capability of continuously monitoring a specific endpoint agent and recording various analytics to detect suspicious system behavior or block malicious activity. In this scenario, your security team would have visibility into analytics related to system behavior, contextual information, and any other activities that justifiably would produce a red flag for your IT department. And most EDR systems nowadays even offer advanced threat detection, investigation, and response capabilities.
Again, in theory, all good stuff. But in practice, we know that cyber attackers don’t stop at one device or server. They will keep coming until they get in.
That’s why USX Cyber has developed our Guardient Extended Detection and Response (XDR) platform. It’s a new approach to cybersecurity, and it’s built on the knowledge that the more data you have, the safer you are.
According to Palo Alto Networks, “While traditional EDR tools focus only on endpoint data, XDR solutions seek to unify siloed security tools to deliver protection, detection, and response across all data sources. An XDR platform integrates endpoint, network, cloud, and third-party data to extend protection, and uses user and entity behavior analytics (UEBA) as well as artificial intelligence (AI) to address some of the known shortcomings of SIEM tools in detecting zero-day attacks.”
XDR solutions provide greater log collection across various data points within the company’s network, giving you an edge over would-be attackers.
The Log Jam Effect
More is good. Until it’s too much.
XDR systems will provide you with a staggering amount of system data. However, being able to source this information in a formatted and digestible manner is one of the leading shortfalls for most cybersecurity products on the market.
To have complete real-time cyber telemetry you need more than just the data logs made available through an XDR cybersecurity system. You need to have the data provided in a way that is digestible, actionable, and integrated into your security suite.
Per John Oltski of CSO, “76% of security professionals say that threat detection and response is more difficult today than it was 2 years ago. Why? Organizations must deal with the volume and sophistication of cyber threats, an increasing cybersecurity workload, and a growing attack surface. Infosec pros also bemoan the fact that they still rely on manual processes and an army of point tools for threat detection and response.”
Guardient was designed specifically to bridge this gap for small businesses. Because the truth of the matter is the data captured by cybersecurity tools is only as good as the output. Today’s cybersecurity professionals are in a constant battle with both hackers and the clock to mitigate breaches before permanent damage is done. And the best tool in this fight for your business is having the right information, right away. Guardient XDR does that. Our state-of-the-art platform includes features like custom alerts, rule decoders and productivity enhancements to streamline your processes — saving you time, money, and damage incurred by cyber attacks.
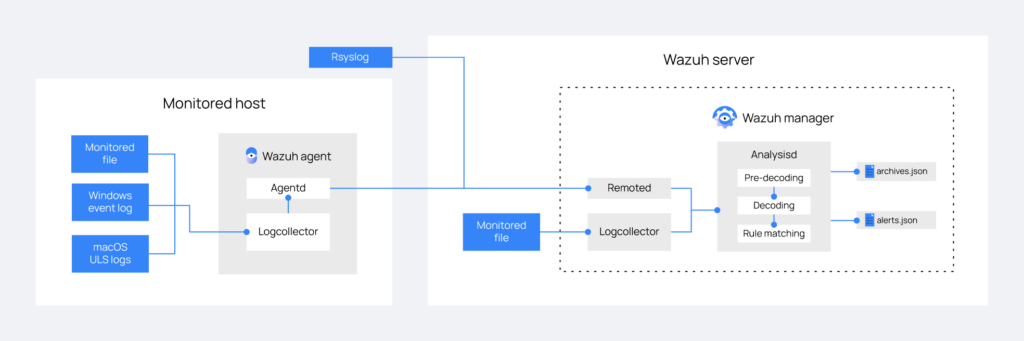
Another critical component of our XDR cybersecurity product is the ability to capture logs created across all devices on your network and the ability to provide real understanding as to what is producing those logs in the first place. Guardient utilizes industry-leading integration tools like Wazuh that allow for simple log collection by pulling files from various endpoint sources, seamless conversion to .json formatting, and intuitive alerts on a SIEM dashboard for instant review. This process can be seen in greater detail below.
Prove It
We don’t fault you for not being prepared for these almost invisible attacks. After all, it’s hard to believe in something you just can’t see with the untrained eye.
But being blissfully unaware is a very dangerous place to be when it comes to your cybersecurity. At USX Cyber, we bear witness to the multitude of attacks that happen daily and hourly to the small-to-medium businesses we proudly protect. And frankly, the data we’ve been collecting proves the sophistication of modern hackers and their desire to target businesses that were previously thought safe.
Now it’s time to see it for yourself.
We’ve created a way you can watch the Guardient XDR platform in action, gathering real-time data about the security of your network. While we firmly believe we’ve developed a security system that provides you the same level of protection that the big corporations employ, it’s important to see it working in your environment and on your devices.
Once you set up your free trial of Guardient XDR, the rest is easy. We’ll walk your IT department through our simple installation process that runs a PowerShell script on a Windows device or Bash script on a Unix/Linux based system. They will even be given the opportunity to review the code for installation to ensure you have a high level of comfort with our product. Guardient will run silently in the background, requiring no upkeep from your IT team and very low resource consumption.
Once the software is up and running, Guardient endpoint agents will be installed — collecting logs through various sources throughout your system(s). Security is obviously paramount, so all data collected is protected in our cloud environment and will be scrubbed after the test is completed. After the trial is complete, USX Cyber’s team of expert analysts will review your data and create a report that allows you to see what Guardient has captured, and more importantly, what your current security software has missed.
Are You Ready? Or not?
There’s no risk to you. The only risk is not knowing. Click here to schedule your completely free trial of our Guardient XDR cybersecurity platform and take the first step in securing your business from cyber threats.













