5 Steps for Improving Remote Work Security: Best Practices to Follow Today
If you’re a business owner, you know that the remote work trend isn’t slowing down. And while there are many benefits to allowing employees to work remotely, there are also real cybersecurity risks that come with it. This makes the need for robust remote work security practices more important than ever before.
In this quick guide, we’ll share some of the best practices for remote work security and steps to follow today to help keep your data and systems secure. Whether your business is just transitioning to a remote work environment or you’ve been remote for a while, smart security procedures can protect your business.
What is remote security?
Remote work security refers to the protocols and measures that a company puts in place to protect its employees who work remotely, i.e., outside of the standard office setting. This can include everything from ensuring that data is properly encrypted and stored on secure servers to providing employees with access to virtual private networks (VPNs) so they can connect to the company network securely.
Today’s dispersed workforces make remote security a crucial component of your small business operations. And while the need is fairly obvious, putting it into practice takes some planning and work. But don’t worry; at USX Cyber, we’ve got you covered with the steps you need to get started.
5 Steps to Improving Remote Work Security
There’s no one-size-fits-all approach when it comes to remote cybersecurity. However, we’ve compiled 5 steps for you to follow today in order to improve your remote work security and begin building a set of best practices.
- Establish a remote security policy.
- Restrict access to sensitive data to authorized users only.
- Use encryption to protect data.
- Use a VPN to connect to the company network remotely.
- Train employees on how to work securely.
1. Establish a remote security policy.
Perhaps the single most important step you can take is establishing a remote security policy. This should include a set of IT security guidelines that govern how employees who work remotely should access and use company resources. The purpose of a remote security policy is to protect an organization’s data and systems from being compromised by unauthorized users, as well as ensure that all remote workers have the necessary tools and training to work securely.
There are many factors you need to consider when creating a remote security policy for your business. The most important factor is the type of data that will be accessed remotely. Other factors include the level of access needed by users, the sensitivity of the data, and the potential for data loss.
2. Restrict access to sensitive data to authorized users only.
Another critical measure you can take to protect your business from data breaches and other security risks is to restrict access to sensitive company data to authorized users only. This means that only employees who need access to the data to do their jobs should be given access and that access should be limited to what is necessary for them to do their work.
Restricting access is important not just because it helps prevent unauthorized users from accessing sensitive data. It also helps ensure that employees are using company resources safely and securely.
3. Use encryption to protect data.
Encryption is key to protecting your small business in a remote work environment. Simply put, encryption is the process of transforming readable data into an unreadable format so that it cannot be accessed by unauthorized users. Encryption should be used both while data is in transit, i.e. being sent over the internet, and when it is stored on servers or devices.
Encrypting data helps protect it from being accessed by unauthorized users, whether they are outside the company or inside the network. It also helps ensure compliance with regulations such as HIPAA and PCI-DSS. So if you handle credit card transactions or operate in the healthcare industry, encryption is all but required to do business.
4. Use a VPN to connect to the company network remotely.
A VPN, also known as a virtual private network, helps to prevent unauthorized access to sensitive information. This extra layer of protection provides a secure connection to the company network, which helps safeguard your data and systems from being compromised. It also allows you to access company resources, such as files and applications, from any location — which is especially relevant with a remote workforce.
There are several different VPN providers available, so it’s important to choose one that meets your needs. The most important factors to consider when choosing a VPN provider are the level of security they offer, the features they provide, and the price.
Once you’ve chosen a VPN provider, the next step is to set up the connection. This process varies depending on the provider you choose but typically involves creating an account and downloading and installing the software. Once installed, you simply open the software and enter your login information to connect to the VPN.
5. Train employees on how to securely work remotely.
Employees are your greatest resource, but they can often be the weakest link in an organization’s cybersecurity defenses. That’s because they may not be aware of the risks posed by cyber threats, or they may not know how to protect themselves and the company from these threats. It’s your job as a business owner to ensure your employees are well-trained on how to securely work remotely.
Training employees on cybersecurity matters is essential for protecting your business from data breaches and other security risks. Employees need to be aware of the dangers posed by cyber threats and know how to protect themselves and the company from these threats. They should also be familiar with the company’s remote security policy and understand how to comply with it. But just as important is drafting your policy so that it is clear and comprehensible for employees of all technical abilities.
The best way to train your employees on cybersecurity is through a combination of online training courses and hands-on training. Online courses can provide employees with a basic understanding of cybersecurity concepts, while hands-on training allows them to apply what they have learned in a safe environment.
Protect Your Remote Business Today
Working remotely can be a great way to attract top talent and give your employees flexibility. However, it is by no means without risk. Running a remote small business requires a specialized cybersecurity plan.
And that’s exactly what USX Cyber specializes in. Whether you do business in-person, in the cloud, or entirely remotely, — our exclusive GuardientTM Extended Detection and Response (XDR) platform stands ready to protect your organization.
Contact one of our expert analysts today to find out how easy it is to get the cyber protection you need.
How Government Subcontractors Can Use Compliance to be More Competitive
The Cybersecurity Maturity Model Certification (CMMC) is a game-changer in the defense industry, and its implementation is on the horizon. While the immediate impact may not be felt on existing contracts, the lack of CMMC compliance could hinder subcontractors from bidding on crucial business opportunities. Let’s explore the value CMMC brings to subcontractors and what these small businesses should do to capitalize.
CMMC Makes Subcontractors a More Attractive Partner
While the government has yet to finalize the CMMC framework, we’re seeing more prime contractors work to proactively achieve compliance and ensure their subcontractor supply chain partners do the same. Many businesses want to avoid problems staffing or completing the work in contracts due to compliance holding up the process.
As a subcontractor, CMMC doesn’t just communicate compliance. It also communicates how seriously you take cyber hygiene in general. This is a demonstration of trust and reliability for potential business partners and new contracts, even if it’s not required. A proactive approach to CMMC compliance today could serve as a strong external validation of your cybersecurity practices overall. Your demonstrated commitment to cybersecurity along with proactive business procedure can really stand out among other bidders.
How Long Does it Take to Get Certified?
There is no set timeline for compliance. In the marketplace, we’re seeing around 6-12 months of work to get to the assessment portion of compliance, but this relies heavily on the business and the pace they want to set.
Because so many of these controls will affect daily and core operations, this timeline can be expedited or delayed based on how quickly these processes can be – or you’d like them to be – incorporated. At USX Cyber, we can get a client to compliance in as quickly as 90 days, but some businesses prefer more time to understand and incorporate the necessary procedures and documentation into their business operations.
This is yet another reason why it’s important for subcontractors not to separate compliance from protection. When you develop a cybersecurity plan with compliance in mind, rather than fixating on a singular piece of the puzzle, your business is holistically starting with a leg up against the competition.
Improving Cybersecurity Posture With CMMC in Mind
When small businesses look for comprehensive cybersecurity solutions that include CMMC, the benefits aren’t just external, they will see advantages in their operations and their bottom line. Rather than pay for cybersecurity and CMMC as separate products, at USX Cyber we advise our clients to develop a singular roadmap that protects their business overall while supporting their need for CMMC compliance. This ensures ongoing protection that takes into account the systems, assets and teams that are part of the dynamic defense your company needs.
Cybersecurity does not have to break the bank for small businesses. Contact us today for a free CMMC consultation and roadmap with our experts.
5 Types of Phishing Scams Employees Need to Watch For
No one is immune to a phishing attack. In fact, even the most tech-savvy individual can fall victim to a clever scam.
Protection starts with education. And as an employee, it’s important for you to be able to identify the different types of phishing scams used by hackers so you can protect yourself and your company from becoming the next victim. Below are five of the most common types of phishing scams to watch out for. But first, let’s take a look at what defines a phishing attack.
What is a phishing scam?
Phishing is a cybercrime in which the perpetrator contacts the target, posing as a legitimate institution, in order to lure them into providing sensitive data. This data can include login credentials, financial information, or other personal data that can be used for identity theft or other malicious purposes.
One of the biggest problems is that phishing attacks can be notoriously difficult to detect, as the perpetrators often use spoofed email addresses and websites that look identical to the real thing.
5 Types of Phishing Scams
While this type of cyber attack has been around for years, phishing scams continue to evolve, making it difficult to keep up with the latest shifts. However, you can reduce your cyber risk by knowing the five common ways that scammers try to trick their targets:
- Spear Phishing
- Executive Phishing
- Smishing
- Vishing
- Angler Phishing
Spear Phishing
This type of email scam is typically initiated by an external threat attempting to leverage personal information for financial gain or identity theft. Spear phishing emails are often hard to spot because they can look like legitimate emails from companies or organizations that you are familiar with. These types of scams usually target individuals who work in finance or accounting, as well as those who work with sensitive information.
To avoid falling victim to a spear phishing scam, be suspicious of any email that asks you for personal or financial information, even if it looks like it’s from a trusted source. If you’re not sure whether an email is real or not, stop immediately and contact the company or organization directly to confirm its authenticity.
Executive Phishing
The second common type of phishing scam is similar to spear phishing, but it targets high-level executives within an organization. The attacker will often impersonate someone in a position of authority, such as the CEO or CFO, in order to get sensitive information from the employees they manage.
Executive phishing emails can be extremely difficult to spot, as they often mimic the writing style of the executives they’re impersonating. These types of scams usually target organizations rather than individuals, and they can have a devastating impact on the company if sensitive information is leaked.
Steering clear of an executive phishing scam means you need to be suspicious of any email that asks you to do something outside of your normal job duties, even if it’s from someone in a position of authority. If you’re not sure whether an email is real or not, contact the person directly to confirm. It’s better to be safe than sorry, especially in this case.
Smishing
While the word might sound made up, smishing is all too real. This type of scam uses text messages instead of emails to try and trick the recipient into giving away sensitive information. Hackers will often pose as a trusted organization, such as a bank or credit card company, and try to get the target to provide login credentials or financial information.
Smishing attacks can be tricky to detect, as text messages from these compromised sources can appear to be legitimate. These types of scams usually target individuals who are less likely to be aware of phishing scams, such as the elderly or those who are not familiar with the technology.
To avoid falling victim to a smishing attack, be suspicious of any text message that asks you for personal or financial information, even if it looks like it’s from a sender you recognize. If you’re not absolutely sure whether the text message is real or not, contact the company or organization directly to confirm.
Vishing
While the name is different, the game is always the same. Vishing uses phone calls instead of emails or text messages to try and trick the recipient into giving away sensitive information. The hacker will often pose as a credible contact, such as a bank or credit card company, and try to get you to provide user names, passwords, or even account information.
Vishing attacks can be tough to spot since phone calls can sound like they’re from someone you know. These types of scams usually go after the same individuals that smishing scams target.
Being a skeptic can help keep you safe from a vishing attack. That means you should be highly suspicious of any phone call that asks you for any sort of confidential information. If you’re not sure whether a phone call is real or not, hang up. It’s not rude; it’s having cyber smarts. You should then call back and ask for confirmation.
Angler Phishing
Angler phishing is catching more and more people due to its novelty. This new type of phishing attack goes after people via social media. In this scam, the attacker pretends to be a customer service representative and uses social engineering techniques to try to trick the user into giving them personal information or access to their account. This type of attack is becoming more common as social media plays an increasingly integral part in our lives.
The best way to thwart an angler phishing attack is to be wary of any unsolicited messages from customer service representatives. Do not click on any links or attachments that they send, and under no circumstance should you give them any personal information. If you are unsure whether a message is on the up-and-up, reach out to the company through their official website or customer service number.
Stay Up to Date on Cybersecurity Risks
Unfortunately, phishing remains one of the most common and dangerous cyber threats that businesses face because hackers know it works. But being vigilant and aware is something we all must do to limit the potential damage. So that means it’s important for you to be able to identify the different types of phishing attacks in order to protect yourself and your company from falling victim.
At USX Cyber, we fulfill our mission of protecting small businesses by keeping you up-to-date on the latest cybersecurity trends. That’s because when you are better informed, you can stay better protected. And as hackers try to find new ways in, you can rest assured that our highly trained cyber analysts have already found a way to stop them. Contact us today to get advanced protection for your business before you need it.
7 Ways to Mitigate Your Business’ Cyber Risk
As a small business owner, you are keenly aware of the many risks your company faces. However, one of the most often overlooked of these risks is cyber security. Despite being one of the most common threats, businesses often do not take the necessary precautions to protect themselves from a cyber attack.
Hackers are always coming up with new ways to exploit vulnerabilities, so it’s important to take steps to protect your business. Here are 7 ways to mitigate your cyber risk:
- Perform a cybersecurity risk assessment
- Install a firewall and keep it up-to-date
- Use strong passwords and change them regularly
- Educate your employees about cyber security best practices
- Consistently update and upgrade your software and systems
- Reduce your attack surface
- Monitor your network for suspicious activity
While there are many cybersecurity measures you can take, implementing even a few of these tips can drastically help reduce your chances of becoming the next victim of a cyberattack.
1. Perform a cybersecurity risk assessment.
A cybersecurity risk assessment is an important tool for businesses to identify areas of vulnerability in their systems and networks. By conducting a robust risk assessment, businesses can identify potential threats and vulnerabilities, and develop plans to mitigate or reduce those risks. Risk assessments can help businesses to better understand their cybersecurity posture and make informed decisions about how to protect their data and systems.
When conducting a risk assessment, businesses should consider the potential impact of a breach, the likelihood of a breach occurring, and the costs associated with recovering from a breach. Risk assessments can be conducted internally or externally, and should be tailored to the specific needs of the business.
2. Install a firewall and keep it up-to-date
A firewall is a critical component of any organization’s cyber security strategy. It helps to protect your network from external threats and can be configured to allow or deny access to specific services and applications. However, your firewall must be kept up to date with the latest security patches and updates to be most effective.
Just as importantly, organizations should also consider implementing a next-generation firewall (NGFW) which offers advanced features such as application control and intrusion prevention. NGFWs can provide a higher level of protection against sophisticated cyber attacks.
3. Use strong passwords and change them regularly
Another way to mitigate the risk of infiltration into your business is to use complex passwords. By using a password that is difficult to guess, you make it more difficult for hackers to gain access to your system.
You can also deploy multi-factor authentication strategies. This means that in addition to a passwordyou will also need another form of identification, such as a fingerprint or an iris scan, to gain access to your system.
A strong policy is just as important as strong passwords.Your policy should discourage password sharing among employees. Not doing so creates a security risk by allowingmultiple people to know the password to a given account. It also makes it difficult to keep track of who is using which password. Finally, if an employee leaves the company, any passwords they know should be changed to prevent them from accessing company information.
4. Educate your employees about cyber security best practices
The best way to mitigate your business’ cybersecurity risk is to train employees regularly on how to identify and avoid cybersecurity threats. By doing so, you can ensure that your employees are aware of the latest threats and know how to protect your business’ data.
Phishing emails are a common risk to your employees and the importance of identifying phishing attempts cannot be understated because of the damage it can cause to your business. Phishing is a type of online fraud that occurs when an attacker tries to trick a victim into providing personal information or financial data. This information can then be used to commit identity theft or other crimes.
Unfortunately, phishing attacks are becoming more sophisticated and harder to spot, so it’s important that your employees know how to identify them. Providing proper training to ensures your employees don’t leave the door open to hackers..
5. Consistently update and upgrade your software and systems
One of the most important things you can do to protect your business from cybercriminals is to apply software updates as soon as they are available. Cybercriminals are constantly looking for ways to exploit vulnerabilities in software, and if you don’t have the latest security updates installed, you could be at risk. That’s why it’s important to check for updates regularly and install them immediately..
To help with this effort, most service and software providers release patches on a regular schedule. Cybercriminals are aware of this and often target organizations that have not implemented an effective patch management schedule. By being aware of when their service or software providers typically release patches, organizations can create an effective patch management schedule and help protect themselves from attacks.
6. Reduce your attack surface
The term “attack surface” refers to the areas of vulnerabilities or entry points that cybercriminals can use to access sensitive information and data. The larger the attack surface, the greater the risk of a successful attack. To reduce the attack surface, organizations need to identify and eliminate as many potential entry points as possible. This can be accomplished through a variety of security measures, including firewalls, intrusion detection/prevention systems, and access control lists. Attack surface reduction is a critical element of any effective security strategy.
An organization’s attack surface can be divided into three categories:
- External attack surface: This includes anything that is publicly accessible, such as websites, email servers, and DNS servers.
- Internal attack surface: This includes anything that is accessible from within the organization’s network, such as file servers, databases, and application servers.
- Endpoint attack surface: This includes anything that is connected to the organization’s network, such as laptops, smartphones, and printers.
The goal of attack surface reduction is to minimize the exposure of all three categories listed above. By doing so, organizations can significantly reduce their risk of a successful cyberattack.
7. Monitor your network for suspicious activity
Being proactive is one of the most effective strategies for mitigating cybersecurity risk. By taking proactive steps to secure your systems and data, you can significantly reduce the likelihood of a successful attack. Implementing strong security controls, such as multi-factor authentication and data encryption, can make it much more difficult for attackers to gain access to your systems and data.
At USX Cyber, we provide advanced cybersecurity, before you need it.. We are able to do that because our GuardientTM platform leverages the most-advanced cybersecurity technologies under the watchful eyes of our US-based analysts. This means your business will be the “first to act” vs. the “last to know” when it comes to cybersecurity threats.
Protect Your Business Today
While following these tips can’t guarantee that your business will be impervious to a cyberattack, they will help you mitigate the risk and make it less likely that your company will be compromised. However, if you’re like many small businesses, you might lack the time, resources or staffing to put these tips into practice. We can help. Contact USX Cyber today and find out how easy it is to get powerful, 24/7 protection that is scaled to fit your business.
How to Securely Manage a Remote Workforce
It wasn’t too long ago that having a remote workforce was the exception. Now, that exception is fast becoming the rule. In fact, the U.S. Census Bureau noted that the number of people primarily working remotely from home has nearly tripled since 2019.
Unfortunately, hackers have taken notice of this growing trend. As more and more companies of all sizes have opened their environments to accommodate remote workers, they’ve often unintentionally opened the door to huge cybersecurity risks.
However, by following our remote work from home security tips you can help ensure your business is set up for success no matter what the future of work looks like.
Top 10 Cybersecurity Tips for Remote Employers
Few, if any, companies were ready for this massive shift to remote work, leaving many IT departments having to play a high stakes game of catch-up. And despite taking proper precautions, shoring up cyber defenses, and following best practices — the overarching truth remains — your people are your greatest cyber risk. Whether that’s through clicking a malicious link from a hacker, or simply not adhering to company security policies, every action by your employees is amplified in this new world of remote work.
But if you follow these 10 actionable cybersecurity tips from our expert USX Cyber analysts, you can help your company and the employees you manage stay protected.
- Work computers are for work only
- Enable user authentication
- Use a VPN
- Have strong password rules
- Keep personal devices off the company network
- Use centralized storage
- Safeguard videoconferences
- Stay on top of software updates
- Follow email best practices
- Establish a cybersecurity plan
1. Work computers are for work only
When remote workers bring a company device home, there may be the temptation to allow other household members (or kids!) to use a laptop, cellphone or other hardware for personal purposes. However, for fairly obvious reasons, this can spell disaster by exposing your network to threats and even unauthorized use of confidential or sensitive files. Yet, this is a fairly easy solution. By making sure your company policy addresses third-party use of company assets, you can avoid this issue.
2. Enable user authentication
Multifactor authentication is a critical tool in defending your network from major security risks. Ideally, remote employees should be required to verify their identity before accessing company data or network resources.
3. Use a VPN
Relying on the security of an individual employee’s network is a dicey proposition at best. VPNs allow secure remote access to company resources, provide encrypted connections and allow access control for your network. They are not a perfect solution. But when combined with these other remote work from home security tips, it can provide a strong layer of protection.
4. Have strong password rules
It’s 2022, and unbelievably “123456” is still the most commonly found password on the dark web, due to data breaches. There are a few simple guidelines you can have your employees follow to strengthen their passwords. This includes using random words and letters, mixing upper and lower case characters, and avoiding passwords that contain dates of birth or nicknames. But an even better plan is to invest in a password manager to keep track of all your employees’ passwords and have them safely stored in an encrypted digital vault.
5. Keep personal devices off the company network
It might not seem like a big risk to allow remote workers to use their personal devices to access your network. But even with antivirus software, password protection, and VPNs — allowing employees to use their own devices on your network is a major oversight. Many of these devices can have outdated software, no password protection or viruses of their own. The best policy here is to require your remote workforce to only use company-issued devices to conduct work-related tasks.
6. Use centralized storage
More and more companies have migrated their files and resources to the cloud, and for good reason. Centralized storage solutions protect files and data via an attached firewall. But when remote employees store files locally, on their devices, data can be lost if that device is compromised or destroyed. Having centralized storage is important, but educating your employees on how to use it is just as crucial.
7. Safeguard videoconferences
Kindly put, meetings can be an acquired taste. And while the new work from home reality has dictated we meet with each other via video conferencing software, it doesn’t come without cybersecurity risks. Since the start of the remote work shift, hackers have been infiltrating video conferences to monitor and gather sensitive company information. On top of that, these “Zoom Bombing” attacks can prove to be quite upsetting to your employees. This means that you need to set up private meetings that are password protected and control guest access through a virtual waiting room.
8. Stay on top of software updates.
You might be picking up on a theme — the simplest security measures are often the most important. Updating software and devices is a huge factor in ensuring your work from home security plan is successful. While most software today will automatically check for security updates and apply them, you still may need to have access to your employee’s remote devices to complete the update fully.
9. Follow email best practices
91% of all cyber attacks start with a phishing email. And while using your company’s inbox against you is one of the most tried and true tactics in a hacker’s toolbox, there are steps you can take to shore up your security. That starts with having robust antivirus software monitoring this attack vector. However, the most important thing you can do when managing your remote workforce is to educate your employees about the dangers and how to spot potential email threats. The old adage holds true, only open email attachments that you are expecting, no matter who sent them.
10. Establish a cybersecurity plan
The number one tip we at USX Cyber give to a potential client is always the same — educate your entire organization on cybersecurity. That starts with having solidified policies, plans, and procedures in place. We’ve seen it time and again be the action that separates successful companies from vulnerable companies. However, it’s critical to ensure these cybersecurity policies are easily understood by every employee. So when you’re building your plan, make sure you frame it with language that is clear and applicable to your remote employee’s workday.
Protect Your Business Today
At USX Cyber, we’ve built our GuardientTM cybersecurity platform to provide small businesses with powerful protection in this new remote working reality. Simply put, the days of treating cybersecurity as optional are over. And just like the internet and email are essential to running a business, the same now goes for having cybersecurity.
With GuardientTM you can have access to the same level of protection the big corporations are using to protect their businesses from remote working risks. But our scalable, flexible, and extensible services make sure you get state-of-the-art cybersecurity that fits both your budget and protection needs.
Talk with a USX Cyber analyst today and let’s navigate this new world together.
Align Cybersecurity with Your Business Goals
Increased profitability. Reduced overhead expenses. Geographical expansion. Better coffee.
Every business has its list of strategic goals and objectives, and hopefully a shared understanding of what they mean and how they impact organizational success. And while these targets are typically defined and driven by the leadership team, they affect everyone, regardless of role or department. It’s easy to see how goals like growth, customer satisfaction, and even internal culture initiatives can benefit the overall success of the business and illicit company-wide support, but there is one area that is often viewed as the sole responsibility of a single department or individual that can actually be the biggest vulnerability within the entire company: cybersecurity.
It may not be easy to see the link cybersecurity has to the success of a business, compared to the more ubiquitous goals and objectives around finances or customer retention, however, spending just a few minutes looking at the many jarring statistics around hackers and the catastrophic outcomes caused by attacks will quickly demonstrate why business leaders should be hyper-focused on this exact topic.

Culture. Trust. Holistic. Cybersecurity Goes Way Beyond ‘Check a Box’.
Enlisting the right approach to cybersecurity requires both a holistic view of a company’s vulnerabilities and weaknesses, as well as overall awareness among employees. It must be a company-wide initiative and every team member should know the risks and best practices. Building a culture that understands the importance of cybersecurity as it relates to the overarching business goals will make implementing these efforts easier and more effective.
Here are some of the benefits of instilling a shared culture and proactive approach to cybersecurity, and how to get started.
- Your data needs a dynamic defense. Warding off hackers is a 27/4 job, and making sure that you have the right tools and skilled people backing your team is key to staying vigilant. USX Cyber’s Managed XDR platform and expert analysts offer a mix of proactive and reactive solutions to keep your IP safe and your data secure. You’ll see what attacks were attempted, and feel safe knowing that there’s a solid plan to deter active threats.
- Your customers demand trust. COVID forced us to move to a world that is predominantly digital, and with that shift came an expectation of privacy and security. Many customers expect their vendors and partners to take the necessary precautions to ensure their customers are safe as a result of their cybersecurity initiatives. Actively communicating that security is a priority of the business is a great way to continually reinforce the trust companies work so hard to build and maintain.
- Your workforce can remain focused. When systems are impacted by ransomware and other forms of cyber attacks, productivity can come to a halt. Technology is impacted of course, but employee focus is also forced to stray from daily activities that keep the business running to thwarting off threats. These unnecessary distractions can cost you in downtime, as well as mismanaged resources.
Laying the Foundation to Continuously Evolve Your Cybersecurity Posture
USX Cyber doesn’t just say we can help – we work with you from the get-go to develop a clear path towards your cybersecurity objectives. Tied directly to your business objectives and ensuring mission performance. Our proven approach addresses both your tactical and strategic needs – giving you cyber-operational support to protect you now, while working with you on continuous improvement activities to set you up for long-term success.
The USX Cyber Road Map provides you with a customized blueprint for how we’ll take your cybersecurity to the next level – and the one after that. On Day 1 we work with you to define where you need to be in the next 12 and 24 months, laying the foundation for an actionable roadmap to continuously evolve and improve your cybersecurity posture.
One of the best ways to measure how your current business goals align with your cybersecurity needs is through an Active Defense Cybersecurity Assessment. Understanding what’s at risk, where your vulnerabilities lie, and formulating a plan of action can feel daunting, but USX Cyber is here to help.
Talk to a USX Cyber expert today to schedule a demo or get your free Active Defense Cybersecurity Analysis.
Build Your Business’ Cybersecurity Fortress with Managed XDR Services
There’s a reason why we don’t build castles anymore to keep us safe. Besides the fact that finding alligators to guard your moat is a pretty dicey proposition. It’s because the protection that towering walls provide vanishes once your defenses are breached. That’s the moment it all comes crashing down.
Unfortunately, this is how many small-and-medium businesses (SMBs) attempt to defend themselves against cyber attacks – relying solely on firewalls and off-the-shelf anti-virus software. The ugly truth of the matter is that businesses need more advanced security tools to be prepared for today’s growing cyber threats.
In fact, it’s estimated that there’s one ransomware attack every 11 seconds. And when SMBs get hit, the results are nothing short of disastrous — nearly 60% of these companies will go out of business within six months of the attack.
Stats like these – and there’s more where they came from – are exactly why USX Cyber has built a dynamic defense that includes Managed Extended Detection and Response (Managed XDR) cybersecurity paired with expert-level human intelligence.
The Right Protection
Simply put, when attackers threaten or get past your preventative tools, you need to deter and destroy them — quickly. Managed XDR detects, analyzes, and responds to bad actors that have infiltrated your system.
But it doesn’t do it with cutting-edge technology alone. It takes the watchful eye of human analysts to unlock the true protection potential of Managed XDR. At USX Cyber we call this “human-led” technology. And it’s the only way to stand up to today’s advanced cyber attacks.
No matter the sector your business is in. No matter your size. You still have to wrestle with the matters of budget constraints, staffing, and limited resources. That’s where Managed XDR can help small businesses protect their turf. It’s unrealistic to expect many IT departments to even have the necessary skills or expertise to stay up-to-date and be prepared for complex cyber threats. When you partner with USX Cyber, you free your staff up from the task of day-to-day security management.
The Right People
There’s no doubt, many of the cybersecurity tools that are available today are brilliantly designed. USX Cyber has enlisted the very best of them in our platform, Guardient, which allows us to keep businesses safe. But as powerful as security software is, it’s only as strong as the humans behind it. That’s because there’s no such thing as impenetrable cybersecurity. Even the best solutions can only be coded to respond to a set of pre-existing rules. So, that means when you rely on technology alone, there’s a good chance you’d never even know an attack happened if hackers were to slip past your system’s triggers.
That’s where knowing the right people truly makes all the difference. Humans are your last line of defense. And our humans (let’s just start calling them analysts) are ready and able to catch the threats that MDR software misses. It’s more than just a complementary approach, Managed XDR is a synergistic defense posture that closes the gaps found in technology and fortifies weak spots to provide enterprise-level protection to businesses that would otherwise find themselves vulnerable.
To run Managed XDR also takes the right training. USX Cyber analysts have decades of combined military, Department of Homeland Security, and FBI experience under their belts. Beyond that, they are experts in the field of cybersecurity and responsible for creating many of the solutions included in your security suite. And our analysts are based right here in the U.S. and available 24/7 to provide human-driven, technology-assisted threat detection. That means you’ll always have access to the elite skill set that our analysts have including threat hunting, eyes-on-glass intelligence, and active response.
The Right Size
You might consider yourself small, but you have a big target on your back. And doing nothing about it truly makes you, and the business you’ve worked tirelessly to grow, a sitting duck. While not being able to staff up your IT department, or having the budget needed to run a robust cybersecurity platform yourself are understandable reasons for bypassing strong security measures — they really aren’t excuses hackers care about.
USX Cyber understands the harsh realities of SMBs and that’s why our GuardientTM Managed XDR offerings were developed to provide a level of protection that is scalable for any budget. It’s also highly extendable to provide security wherever you do business — in the cloud, on your server, or in any environment.
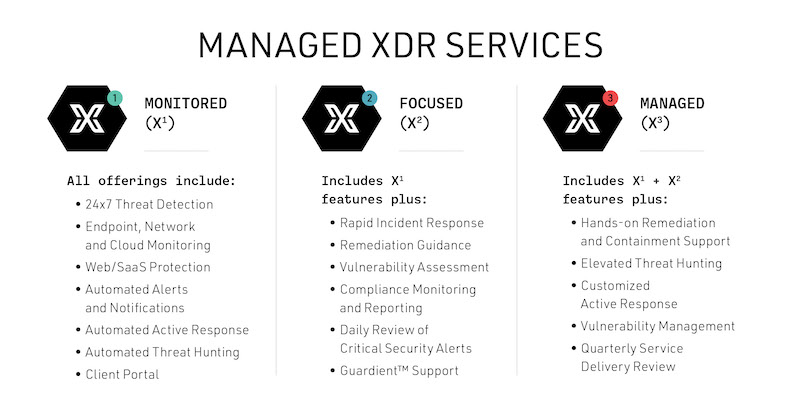
GuardientTM allows for customization to fit your needs with a tiered product offering that includes X1 Monitored, X2 Focused and X3 Managed levels of service. But no matter the level of protection you choose, you can rest easy in the knowledge that all are backed by our highly trained USX Cyber analysts.
Guard Against it All
It’s OK if you’re not an expert in cybersecurity — it’s a lot to take in. On top of that, you’re tasked with running a business, which means your focus is spread across many disciplines. But the threat of ransomware, phishing scams, data breaches, and denial of service attacks are very real and require your attention, too.
USX Cyber offers the right-sized protection your business needs to stay guarded in this new world of cyber vulnerability. By putting the right technology and the right people on your side, you can be confident you have a solution that works.
Or by all means, go with the gators.
Talk to a USX Cyber expert today to schedule a demo or get your free Active Defense Cybersecurity Analysis.













