Revolutionizing Cybersecurity with AI-Driven Critical Alert Analysis
In today’s dynamic cybersecurity landscape, the sheer volume and complexity of alerts can overwhelm even the most skilled analysts. To address this challenge, USX Cyber has integrated cutting-edge artificial intelligence (AI) into its GUARDIENT™ XDR platform. This integration marks a significant leap forward in how security alerts are analyzed, empowering analysts with real-time, intelligent insights while ensuring sensitive information remains protected.

The Role of AI in Modern Cybersecurity
The modern threat landscape is characterized by sophisticated attacks that evolve rapidly, making it increasingly difficult for traditional cybersecurity measures to keep pace. Analysts are oftentimes inundated with alerts, many of which may be false positives or low-priority events. This overwhelming volume can lead to critical alerts being overlooked or response delays, putting organizations at significant risk.
To combat this, GUARDIENT™ leverages AI to enhance the efficiency and effectiveness of alert analysis. By automating the assessment process, AI allows security teams to focus on the most pressing threats, improving response times while reducing the risk of human error.
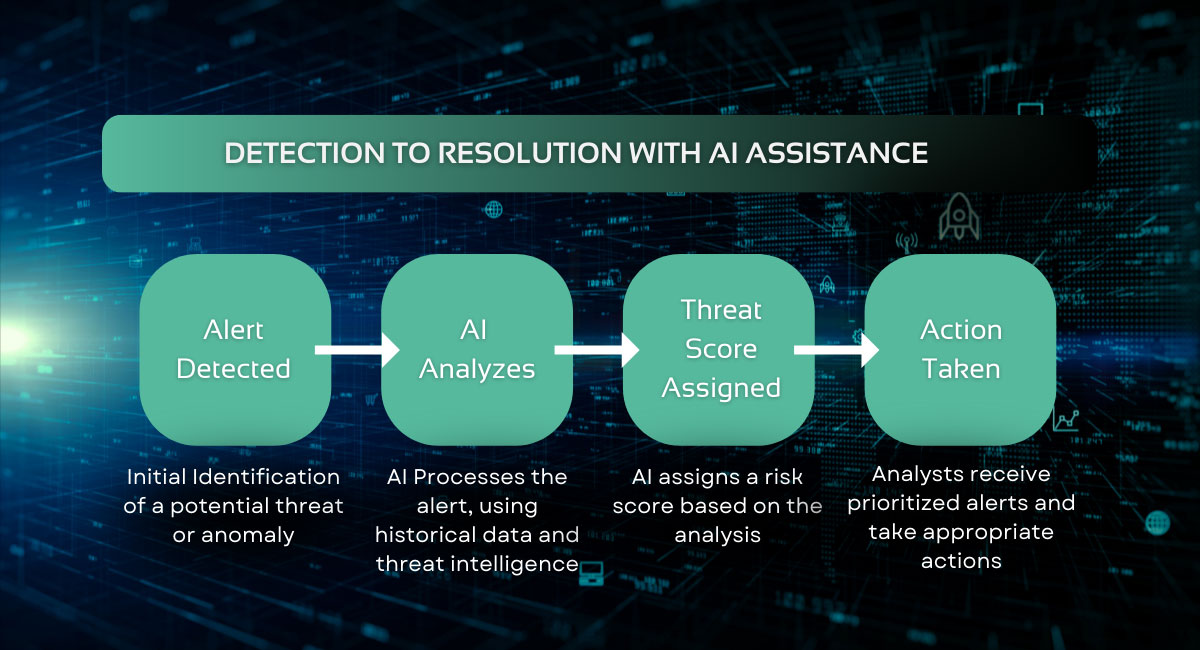
AI-Enhanced Critical Alert Analysis
The AI integration within GUARDIENT™ is designed to intelligently analyze security alerts by evaluating historical attack patterns, threat intelligence, and known indicators of compromise (IoCs). The AI provides a comprehensive assessment of each alert, assigns a threat likelihood score, highlights relevant historical context, and identifies potential IoCs.
This analysis provides analysts with the essential information needed to make swift, informed decisions, while also offering recommendations for further investigation or immediate action. The AI’s ability to learn from historical data ensures that it remains effective even as threats evolve.
Key Benefits of AI Integration
- Increased Efficiency: AI significantly reduces the time analysts spend on triaging alerts by automating the analysis process.
- Enhanced Accuracy: The AI’s assessments are grounded in extensive historical data and threat intelligence, providing more reliable threat detection.
- Proactive Threat Management: With the ability to recognize patterns and predict potential threats, the AI supports a proactive approach to cybersecurity.
- Scalability: The AI-driven analysis is scalable, making it suitable for organizations of any size, from SMBs to large enterprises.
The integration of AI into the GUARDIENT™ XDR platform represents a transformative step forward in cybersecurity. By automating critical alert analysis and providing actionable insights, USX Cyber is helping organizations stay ahead of the ever-evolving threat landscape. This AI-driven approach not only enhances the capabilities of security teams but also ensures that sensitive data remains protected, underscoring GUARDIENT™’s position as a leader in advanced cybersecurity solutions.
Challenges for MSPs in Offering Cybersecurity Solutions
In an increasingly digital world, cybersecurity has become a paramount concern for businesses of all sizes. Managed Service Providers (MSPs) are often on the frontline, trying to satisfy the cybersecurity needs of their clients. However, the rapidly evolving landscape of cyber threats and the complexity of modern IT environments present significant challenges for MSPs. This article explores these challenges and how MSPs can navigate them to provide robust cybersecurity services.

Rapidly Evolving Threat Landscape
One of the primary challenges MSPs face is keeping up with the fast-paced evolution of cyber threats. Cybercriminals are continually developing new techniques to breach security defenses, from sophisticated phishing attacks to ransomware and zero-day exploits. This dynamic environment requires MSPs to constantly update their knowledge and tools to stay ahead of potential threats.
Complexity of IT Environments
Modern IT environments are complex, often encompassing a mix of on-premises and cloud-based systems, multiple devices, and various third-party applications. This complexity makes it difficult for MSPs to maintain a unified security posture. Each component of the IT infrastructure can present unique vulnerabilities, necessitating a comprehensive and integrated approach to cybersecurity.
Resource Constraints
Many MSPs, especially smaller ones, face resource constraints that make it challenging to deliver effective cybersecurity solutions. Hiring and retaining skilled cybersecurity professionals is costly and competitive. Additionally, investing in advanced cybersecurity tools and technologies can strain budgets. This resource gap can limit the ability of MSPs to provide the level of security that their clients demand.
Regulatory Compliance
Navigating the myriad of regulatory requirements related to cybersecurity can be daunting. Different industries and regions have specific regulations that dictate how data should be protected and reported in the event of a breach. MSPs must ensure their services comply with regulations such as GDPR, HIPAA, CMMC and CCPA, which requires a thorough understanding of these laws and the implementation of appropriate measures to meet compliance standards.
Client Education and Expectations
Many clients may not fully understand the complexities and importance of robust cybersecurity measures. MSPs frequently dedicate substantial time to educating their clients about potential risks and essential precautions. Additionally, clients may have unrealistic expectations regarding the cost and effectiveness of cybersecurity solutions, expecting comprehensive protection at minimal cost.
Integration with Existing Systems
Integrating new cybersecurity solutions with a client’s existing systems can be challenging. Legacy systems may not be compatible with modern security tools, and the process of integration can disrupt business operations. MSPs must carefully plan and execute integration projects to minimize downtime and ensure seamless operation.
Incident Response and Recovery
When a cyber incident occurs, the pressure on MSPs to respond swiftly and effectively is immense. Incident response requires a well-coordinated approach, including identifying the breach, containing it, eradicating the threat, and recovering systems. MSPs must have robust incident response plans and the ability to quickly mobilize resources to mitigate damage and restore normal operations.
Trust and Reputation Management
Maintaining trust is critical for MSPs offering cybersecurity services. A single security breach can significantly damage an MSP’s reputation, leading to loss of clients and revenue. MSPs must continuously demonstrate their commitment to security and reliability, ensuring that they can deliver on their promises.
Obtaining, Maintaining Cyber Insurance and Successfully Filing a Claim
MSPs must offer cybersecurity solutions that meet insurers’ demands for detailed information about their clients’ cybersecurity measures. They also need to continually assist clients in maintaining strict cybersecurity protocols, such as multi-factor authentication and regular security audits. The rapidly evolving nature of cyber threats makes it challenging to keep security measures up-to-date, a critical factor for obtaining and maintaining insurance coverage.
Strategies for Overcoming Challenges
To address these challenges, MSPs can adopt several strategies:
- Continuous Education and Training: Regularly updating skills and knowledge through training and certifications helps MSPs stay current with the latest cybersecurity trends and technologies.
- Investing in Advanced Tools: Allocating resources to invest in advanced cybersecurity tools and technologies can enhance an MSP’s ability to protect their clients effectively.
- Building Strong Vendor Partnerships: Collaborating with reputable cybersecurity vendors can provide access to cutting-edge solutions and support.
- Developing Comprehensive Incident Response Plans: Having detailed and tested incident response plans ensures that MSPs can quickly and effectively handle security incidents.
- Client Communication: Educating clients about cybersecurity risks and setting realistic expectations for security solutions can foster better client relationships and trust.
- Focus on Compliance: Staying informed about regulatory changes and integrating compliance requirements into service offerings can help MSPs ensure that their solutions meet legal standards.
While the challenges MSPs face in offering cybersecurity solutions are significant, they are not insurmountable. By choosing USX Cyber, MSPs can be assured of a cybersecurity partner offering a holistic cybersecurity solution tailored to meet their unique needs and demands of today’s digital landscape. Here’s why USX Cyber stands out:
- GUARDIENT™™-Powered Security: USX Cyber offers GUARDIENT™, a robust fully integrated, state-of-the-art XDR security tool providing unparalleled protection against cyber threats. GUARDIENT™’s advanced capabilities ensure comprehensive monitoring, detection, and response to potential security incidents. It saves money by eliminating tool sprawl. USX Cyber can also provide supporting outsourced specialized cybersecurity services and serve as a third-party SOC to extend your cyber capabilities.
- Expertise and Continuous Education: At USX Cyber, our U.S. team of cybersecurity professionals is continuously trained and certified in the latest security trends and technologies, ensuring we stay ahead of emerging threats, so you don’t have to.
- Advanced Tools and Technologies: Beyond GUARDIENT™, we invest in complementary cybersecurity tools to provide you with the most robust defense mechanisms to help protect your clients.
- Strong Vendor Partnerships: Our collaborations with leading cybersecurity vendors ensure access to innovative solutions and support, enhancing the continual efficacy of Guardient.
- Comprehensive Incident Response Plans: USX Cyber has developed a library of over 150 detailed and tested incident response plans (X-MattersTM ) enabling our cyber defenders to respond swiftly and effectively to any security incident.
- Client Education and Transparent Communication: We prioritize educating our partners and clients about cybersecurity risks and setting realistic expectations, fostering trust and strong relationships.
- Regulatory Compliance Expertise: We stay informed about regulatory changes and integrate compliance requirements into our solution and service offerings, ensuring you can help your clients become and remain compliant.
By choosing USX Cyber, MSPs can confidently navigate the complexities of cybersecurity, knowing they are protected by a partner committed to excellence, innovation, and reliability. With GUARDIENT™ at the core of our security solutions, USX Cyber provides unmatched protection and peace of mind. Let USX Cyber be your trusted ally in securing you and your clients’ digital future.
Tackling Security Tool Sprawl: The Path to Streamlined Security
In the modern cybersecurity landscape, organizations are grappling with a complex and pressing issue: security tool sprawl. This term refers to the proliferation of various cybersecurity tools within an organization, often resulting from the need to address a wide range of cyber threats. While having a variety of tools may seem beneficial, unchecked security tool sprawl can create significant challenges and risks for organizations.

The Causes of Security Tool Sprawl
Security tool sprawl often arises from the following factors:
- Vendor Proliferation: The cybersecurity market is crowded with various vendors offering specialized tools for specific security challenges. This abundance of options can lead organizations to adopt multiple tools to cover different aspects of their security needs.
- Evolving Threat Landscape: Cyber threats are constantly changing and becoming more sophisticated. Organizations may feel the need to continuously add new tools to address emerging threats, resulting in tool sprawl.
- Lack of Centralized Management: When different departments or teams within an organization independently select and implement security tools, it can lead to redundancy and inefficiency.
- Legacy Systems: Older tools may still be in use despite offering limited value. This can contribute to the overall sprawl problem, especially if newer, more effective tools are available.
The Impact of Security Tool Sprawl
Unchecked security tool sprawl can have significant negative effects on an organization’s security operations:
- Increased Complexity: Managing a large number of disparate tools can be overwhelming for security teams, making it difficult to maintain an effective security posture.
- Fragmented Visibility: Multiple, unintegrated tools can hinder a comprehensive view of the organization’s security status, making it harder to detect and respond to threats.
- Higher Costs: Maintaining and supporting a multitude of tools, including licensing and training costs, can quickly become expensive.
- Reduced Efficiency: Overlapping functionalities among tools can lead to confusion and reduced productivity for security teams.
- Increased Risk: Inconsistent monitoring and coverage across different tools may create security gaps, leaving the organization vulnerable to breaches.
Strategies for Consolidation and Management
To combat security tool sprawl, organizations can adopt strategies for effective consolidation and management:
- Assessment of Current Tools: Conduct a comprehensive evaluation of existing tools to identify redundancy and determine which tools are truly necessary for the organization’s security needs.
- Standardization and Integration: Aim to standardize tools across the organization and prioritize those that offer broad functionality and seamless integration with other systems.
- Centralized Management: Use a unified platform or tool to manage all security functions, streamlining processes and providing a more holistic view of the security landscape.
- Cloud-Based Solutions: Consider leveraging cloud-based security solutions that offer scalability and the ability to consolidate multiple functions within a single platform.
- Continuous Evaluation: Regularly review and adjust the organization’s security strategy and toolset to ensure optimal performance and protection.
Security tool sprawl presents significant challenges for organizations, from increased complexity and costs to potential security gaps. Streamlining and consolidating tools is essential for an efficient, effective security posture. One notable solution that addresses these challenges is GUARDIENT™™ a comprehensive platform designed to consolidate multiple security tools into a unified solution.
GUARDIENT™ offers a single view of all security data, enabling security teams to monitor, manage, and respond to threats with ease and precision. By integrating various security functions into one centralized platform, GUARDIENT™ simplifies workflows, enhances visibility, and optimizes resource utilization.
Embracing solutions like GUARDIENT™ empowers organizations to gain a holistic understanding of their security posture, improve efficiency, and strengthen defenses against ever-evolving cyber threats. By reducing security tool sprawl and consolidating data within a single, accessible platform, organizations can take proactive and effective measures to safeguard their digital environments.
What You Don’t Know Will Hurt You: Understanding Real-Time Cyber Telemetry
Data is the very lifeblood of businesses big or small — from the financial data that helps steer organizational decisions to the customer data you are charged with safekeeping. But data is also your best defense against cyber attackers. That is if you know how to harness it correctly.
Real-time cyber telemetry is how USX Cyber puts your data to work and helps you stay protected in today’s environment of rapidly evolving cyber threats. Simply put, real-time cyber telemetry is the collection of data across multiple points such as endpoints (individual computing device), a network, email server, and the cloud to actively aid in the detection and hunting of cyber threats.
This is the foundation for our leading-edge Guardient Extended Detection and Response (XDR) cybersecurity platform. By gathering comprehensive security data from your organization as a whole, we are able to get a much more complete picture of your network than a traditional Endpoint Detection and Response (EDR) model could ever provide (more on that in a second). Guardient also brings together industry-leading tools and Analysts to provide instant, actionable insights to help defend your business against hackers and other threats.
Let’s take a deeper look at why XDR and telemetry provide unmatched protection.
More Data is Needed
Traditional cybersecurity products have generally fallen under the umbrella of the EDR model. In this defense posture, an agent is installed locally on a system, and alerts are captured only for the endpoint that is being monitored. This is known as a Host Intrusion Detection System (HIDS) and it is a very common practice in the cybersecurity industry. And there’s nothing theoretically wrong with this methodology. HIDS has the capability of continuously monitoring a specific endpoint agent and recording various analytics to detect suspicious system behavior or block malicious activity. In this scenario, your security team would have visibility into analytics related to system behavior, contextual information, and any other activities that justifiably would produce a red flag for your IT department. And most EDR systems nowadays even offer advanced threat detection, investigation, and response capabilities.
Again, in theory, all good stuff. But in practice, we know that cyber attackers don’t stop at one device or server. They will keep coming until they get in.
That’s why USX Cyber has developed our Guardient Extended Detection and Response (XDR) platform. It’s a new approach to cybersecurity, and it’s built on the knowledge that the more data you have, the safer you are.
According to Palo Alto Networks, “While traditional EDR tools focus only on endpoint data, XDR solutions seek to unify siloed security tools to deliver protection, detection, and response across all data sources. An XDR platform integrates endpoint, network, cloud, and third-party data to extend protection, and uses user and entity behavior analytics (UEBA) as well as artificial intelligence (AI) to address some of the known shortcomings of SIEM tools in detecting zero-day attacks.”
XDR solutions provide greater log collection across various data points within the company’s network, giving you an edge over would-be attackers.
The Log Jam Effect
More is good. Until it’s too much.
XDR systems will provide you with a staggering amount of system data. However, being able to source this information in a formatted and digestible manner is one of the leading shortfalls for most cybersecurity products on the market.
To have complete real-time cyber telemetry you need more than just the data logs made available through an XDR cybersecurity system. You need to have the data provided in a way that is digestible, actionable, and integrated into your security suite.
Per John Oltski of CSO, “76% of security professionals say that threat detection and response is more difficult today than it was 2 years ago. Why? Organizations must deal with the volume and sophistication of cyber threats, an increasing cybersecurity workload, and a growing attack surface. Infosec pros also bemoan the fact that they still rely on manual processes and an army of point tools for threat detection and response.”
Guardient was designed specifically to bridge this gap for small businesses. Because the truth of the matter is the data captured by cybersecurity tools is only as good as the output. Today’s cybersecurity professionals are in a constant battle with both hackers and the clock to mitigate breaches before permanent damage is done. And the best tool in this fight for your business is having the right information, right away. Guardient XDR does that. Our state-of-the-art platform includes features like custom alerts, rule decoders and productivity enhancements to streamline your processes — saving you time, money, and damage incurred by cyber attacks.
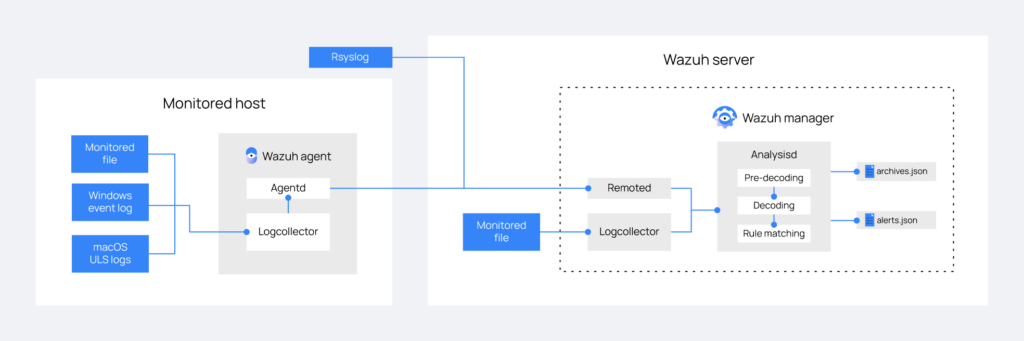
Another critical component of our XDR cybersecurity product is the ability to capture logs created across all devices on your network and the ability to provide real understanding as to what is producing those logs in the first place. Guardient utilizes industry-leading integration tools like Wazuh that allow for simple log collection by pulling files from various endpoint sources, seamless conversion to .json formatting, and intuitive alerts on a SIEM dashboard for instant review. This process can be seen in greater detail below.
Prove It
We don’t fault you for not being prepared for these almost invisible attacks. After all, it’s hard to believe in something you just can’t see with the untrained eye.
But being blissfully unaware is a very dangerous place to be when it comes to your cybersecurity. At USX Cyber, we bear witness to the multitude of attacks that happen daily and hourly to the small-to-medium businesses we proudly protect. And frankly, the data we’ve been collecting proves the sophistication of modern hackers and their desire to target businesses that were previously thought safe.
Now it’s time to see it for yourself.
We’ve created a way you can watch the Guardient XDR platform in action, gathering real-time data about the security of your network. While we firmly believe we’ve developed a security system that provides you the same level of protection that the big corporations employ, it’s important to see it working in your environment and on your devices.
Once you set up your free trial of Guardient XDR, the rest is easy. We’ll walk your IT department through our simple installation process that runs a PowerShell script on a Windows device or Bash script on a Unix/Linux based system. They will even be given the opportunity to review the code for installation to ensure you have a high level of comfort with our product. Guardient will run silently in the background, requiring no upkeep from your IT team and very low resource consumption.
Once the software is up and running, Guardient endpoint agents will be installed — collecting logs through various sources throughout your system(s). Security is obviously paramount, so all data collected is protected in our cloud environment and will be scrubbed after the test is completed. After the trial is complete, USX Cyber’s team of expert analysts will review your data and create a report that allows you to see what Guardient has captured, and more importantly, what your current security software has missed.
Are You Ready? Or not?
There’s no risk to you. The only risk is not knowing. Click here to schedule your completely free trial of our Guardient XDR cybersecurity platform and take the first step in securing your business from cyber threats.
